Wednesday, 21 November 2012
Social Engineering - Study Of Breaking Network Security Through Manipulation
Social engineering is a nontechnical method of breaking into a system or network. It's the process of deceiving users of a system and convincing them to give out information that can be used to defeat or bypass security mechanisms. Social engineering is important to understand because hackers can use it to attack the human element of a system and circumvent technical security measures. This method can be used to gather information before or during an attack.
The following is an example of social engineering recounted by Kapil Raina, currently a security expert at Verisign, based on an actual workplace experience with a previous employer. "One morning a few years back, a group of strangers walked into a large shipping firm and walked out with access to the firm's entire corporate network. How did they do it? By obtaining small amounts of access, bit by bit, from a number of different employees in that firm. First, they did research about the company for two days before even attempting to set foot on the premises. For example, they learned key employees' names by calling HR. Next, they pretended to lose their key to the front door, and a man let them in. Then they "lost" their identity badges when entering the third floor secured area, smiled, and a friendly employee opened the door for them. The strangers knew the CFO was out of town, so they were able to enter his office and obtain financial data off his unlocked computer. They dug through the corporate trash, finding all kinds of useful documents. They asked a janitor for a garbage pail in which to place their contents and carried all of this data out of the building in their hands. The strangers had studied the CFO's voice, so they were able to phone, pretending to be the CFO, in a rush, desperately in need of his network password. From there, they used regular technical hacking tools to gain super-user access into the system. In this case, the strangers were network consultants performing a security audit for the CFO without any other employees' knowledge. They were never given any privileged information from the CFO but were able to obtain all the access they wanted through social engineering."
The most dangerous part of social engineering is that companies with authentication processes, firewalls, virtual private networks, and network-monitoring software are still wide open to attacks, because social engineering doesn't assault the security measures directly. Instead, a social-engineering attack bypasses the security measures and goes after the human element in an organization.
Easiest Hacking Trick - Manipulation
We all, who have not yet tasted the fun of hacking, have a misconception that hacking needs a mastery on programming languages and logical skills.
But its neither truth nor false.
Yes hacking needs these two weapons. But there is a style of hacking which requires a much required technical skilland more of a coning skill. This style is well known as MANIPULATION.
An example of the using the art of manipulation is illustrated in the following example. The facilitator of a live Computer Security Institute demonstration showed the vulnerability of help desks when he dialed up a phone company, got transferred around, and reached the help desk. "Who's the supervisor on duty tonight?" "Oh, it's Betty." "Let me talk to Betty." [He's transferred.] "Hi Betty, having a bad day?" "No, why?…Your systems are down." She said, "my systems aren't down, we're running fine." He said, "you better sign off." She signed off. He said, "now sign on again." She signed on again. He said, "we didn't even show a blip, we show no change." He said, "sign off again." She did. "Betty, I'm going to have to sign on as you here to figure out what's happening with your ID. Let me have your user ID and password." So this senior supervisor at the help desk tells him her user ID and password. In a few minutes a hacker is able to get information that might have taken him days to get by capturing traffic and cracking the password. It is much easier to gain information by social engineering than by technical methods. People are usually the weakest link in the security chain. A successful defense depends on having good policies in place and teaching employees to follow the policies. Social engineering is the hardest form of attack to defend against because a company can't protect itself with hardware or software alone.
Saturday, 17 November 2012
Top 5 Free Keyloggers Techno Teenz
I was just finding a good KEYLOGGER as requested by a friend and I was stunned to see that its like finding a needle in a haystack to find a good KEYLOGGER thats free of cost. Here after much effort is the list that may help you.
Note: you wont be able to use the right click in my blog so just select the download linc and paste it on address bar.
5 Free Keyloggers to monitor your
Local PC or Laptop!
Here is an exclusive list of top 10 free
local keyloggers. However If you are
planning to monitor only your PC or any
PC which you have control of, then you
can blindly go for "Hardware
Keyloggers" as they are the safest
keyloggers and operate in a complete
stealth. If you Still wanna Prefer Free
Keyloggers then below is the list of
Free keyloggers that will really help
you monitor your PC.
1) REFOG Free Edition
Refog Free Keylogger beats
competition in two respects: it's simple
to use and it's free. REFOG Free
Keylogger can look after your children
without them even noticing. Even
technically minded children won't
detect the key logger when it runs in a
stealth mode. The program removes all
the shortcuts and can be accessed only
through a hot key combination.
Running unobtrusively from the
moment the system boots, REFOG Free
Keylogger keeps track of all typed or
pasted text.
Download link: http://www.refog.com/
trial2.html or click here
2) Black box express
Simple to use monitoring of one local
computer; Monitor Screen recordings,
Programs, Keystrokes typed, Websites,
Web Searches, Emails/Webmails/
Instant Messenger Chat sent and
received. Alerts and Warnings instantly
or as a summary on your e-mail or cell
phone. everything for 100% Free. No
strings attached.
Download link: www.asmsoftware.com/
MyAccount/Downloads/
Download.ashx?ProductId=1c3ff8b2-
f4c6-434e-9810-95de152cdce0 OR click here
3) Personal keylogger
The Personal Keylogger application was
designed to be a small tool that will
allow you to secretly record all
keystrokes and other input. All specific
instructions are explained in the
application. To exit it and receive your
logs, you will need to enter in your
keycode. If you have forgotten your
keycode, you will need to restart the
computer. Keycode is like password. To
stop Personal keylogger, you can enter
your keycode anywhere on the screen.
Once you type-in your keycode, the
keylogger will stop monitoring and the
log.txt file will be created in your
selected destination folder.
Download link: www.nfyre.com/prog/
Personal%20Keylogger.zip OR click here
4) Py keylogger
PyKeylogger is an easy-to-use and
simple keylogger written in python. It is
primarily designed for backup
purposes, but can be used as a stealth
keylogger, too. It does not raise any
trust issues, since it is a short python
script that you can easily examine. It is
primarily designed for personal backup
purposes, rather than stealth
keylogging. Thus, it does not make
explicit attempts to hide its presence
from the operating system or the user.
That said, the only way it is visible is
that the process name shows up in the
task list, so it is not immediately
apparent that there is a keylogger on
the system.
#Tip: Press and hold 'left-CTRL + Right-
CTRL + F12′ keys simultaneously to
bring up the Control Panel (default
password is blank).
Download link: http://sourceforge.net/
projects/pykeylogger/files/
pykeylogger/1.2.1/pykeylogger-1.2.
1_win32_installer.exe/download OR click here
5) Heretic Macro
Heretic is a powerful tool that is able to
record user events, such as mouse
clicks and keys, into a C/Java-like
script, and play that script either once
or repeatedly. It has many commands
for dynamic pixel-based botting,
window based botting, and static
botting/macro-ing (i.e. key presses,
mouse clicks, mouse moves, and
pauses).
Download link: http://zone-dev.com/
downloads/Hereticsetup.exe OR click here
Monday, 12 November 2012
***Registry Hack to Tweak Your Windows PC*** Disable USB Devices
Microsoft Windows offers a feature-rich interface and several customization options that make it one of the most user friendly operating systems in the world. However, computer geeks would still love to hack the Windows Registry so as to add more extra features and functionalities to their operating system.
If you're one such geek who would like to customize Windows in your own way, here is a list of 8 interesting registry hacks that you need to try:
1. Disable USB Devices:
Disabling USB ports can be a smart idea
to add security to the computer. This
can be really handy if the computer is
on a public place where the chances of
virus and other malware infection is
really high. You can easily disable
access to USB ports with the following
registry hack:
Open the Registry Editor (Start -> Run -
> Type regedit and hit Enter)
In the registry, navigate to the
following key:
HKEY_LOCAL_MACHINE\SYSTEM\Curr
entControlSet\Services\UsbStor
In the right-side pane, double-click on
"Start".
In the "Value data" field enter 4 and
click on "OK".
Close the Registry Editor and reboot.
To enable USB devices, follow the same
procedure as above except in the
step-4 enter 3 in the "Value data" field.
Works on Windows XP, Vista and 7.
Saturday, 10 November 2012
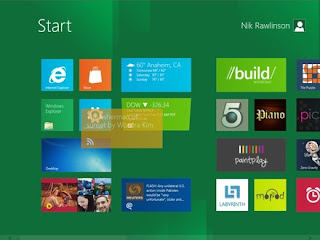
START MENU in Windows8 - A confusing stop
Office 2010 Recommends Windows 8 Users to Click on the "Start Menu" Windows 8 is considered one of the most confusing Windows versions ever released by Microsoft, mostly because it doesn't comprise the traditional Start Menu available since the debut of Windows 95. Instead, Windows 8 comes with a Start Screen, but Office 2010 advises users to launch the built-in apps, such as Word, by clicking on the Start Menu. Now, we know that this has nothing to do with Microsoft and the Office 2010 installer was designed when Windows still had a Start Menu, but given the fact that Windows 8 adopters are confused by every minor modifications on their computers, such a thing would only make things worse. So, in case you've already deployed Windows 8 on your computer and you plan to use Office 2010 too, the installer is just outdated. Don't trust it, there's no such thing as a Start Menu in Windows 8!
Thursday, 8 November 2012
3G Hack - Unlimited 3G free on DOCOMO
Hia Fellas I guess you all have been waiting for a rockig trick just to chill around in network world in a better way. Till previous month I was just fed up of the slow speed internet in my mobile. No matter I buy an expensive set or a new sim the 2G speed iritates me.
Here is what I actually did. OMG!!! Till now my download speed in mobile varies from 500kbps to 1000kbps.
Here are the simple steps that will clear all fog that has been created by search results till now.
REQUIREMENTS
1. Tata Docomo SIM Card with
a balance of more than Rs. 1
2. 3G enabled cellphone
STEPS
1. Create New Access Point
Using Below Configuration
and restart your cellphone.
Name : Tata Docomo
or any
Access Point ( APN )
–
tata.docomo.dive.in
Homepage :
www.google.com or
any
Proxy :
202.87.41.147
Proxy Port : 8080
Username : leave
blank
Password : leave
blank
2. Download Operamini 4.2
Handler Browser that you will find
here
www.plunder.com/
OperaMini4-2HandlerMod-jar-
download-7317b80fa2.htm
3. Open your Opera mini
handler and do the
following changes in the
Setiings:
• Set Divein Settings
as Default Settings
• For Opera Mini
Set http in Custom
Field in your Opera
Mini handler
• Set Socket Server to
http://203.115.112.5.server4.
operamini.com
OR
http://10.124.72.171.server4.
operamini.com
• Keep Proxy Type as
blank (Don't Enter
Anything in Proxy
Server Field)
4. Done!! Now use your free
unlimited 3G service.
Enjoy!!
Subscribe to:
Comments (Atom)